Downloads
Keywords:
Zero Trust in Practice: How Enterprises Are Implementing Zero Trust Architectures Across Multi-Cloud System
Authors
Abstract
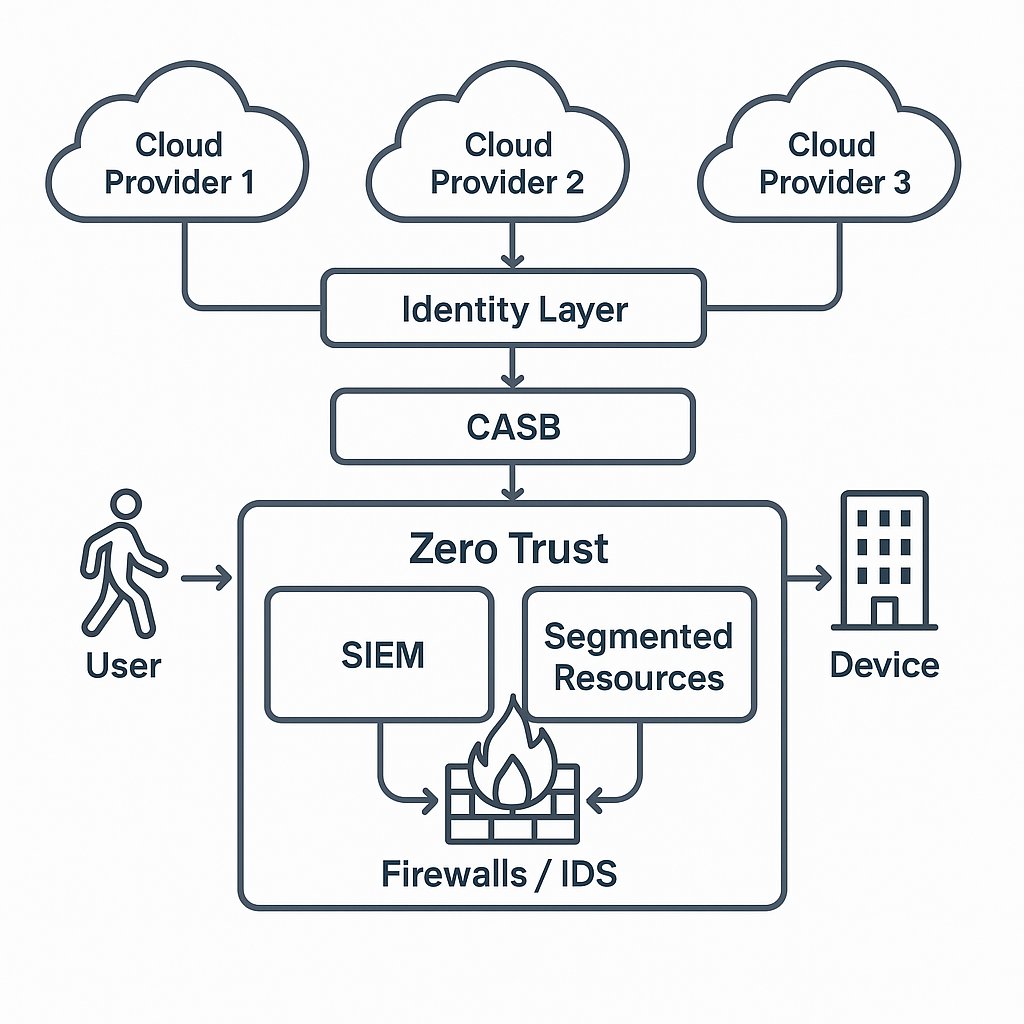
In the new age and era of cyber threats that are advancing by the day, the mere security structures that were able to safeguard enterprise information, particularly in the complicated multi-cloud structures, have become outdated. Zero Trust (ZT) architecture, with its core principle, which is never trusted, always verified, has become one of the most viable security frameworks to leverage these challenges. This study examines how companies implement zero-trust architectures to safeguard their multi-cloud infrastructures. It explores the fundamental concepts of Zero Trust, such as identity and access management, micro-segmentation and continuous monitoring, and the practical tools that help implement Zero Trust. Case studies included in this paper will represent examples of the adoption of Zero Trust in the real world, as well as challenges and benefits. Moreover, it discusses future patterns of the Zero Trust architecture, including AI and machine learning. It provides guidelines to admit organizations that want to adopt Zero Trust to work in multifarious clouds. The research highlights the need for a layered and strategic security approach and presents a blueprint for companies interested in improving their cloud security standing.



